Kubernetes
Kubernetes is an open‑source platform for managing clusters of container applications and services. Kubernetes was developed in 2014 by Google engineers Joe Beda, Brendan Burns, and Craig McLuckie. It was shortly thereafter released as open source. Today, Kubernetes—whose name means “helmsman” or “pilot” in ancient Greek—is managed by the Cloud Native Computing Foundation (CNCF), a project of the Linux Foundation.
Description¶
Pods
A Kubernetes pod is the smallest deployable unit you can run within Kubernetes. A pod is a group of one or more containers that share the same storage and/or network resources. Each Kubernetes pod has a unique IP address and persistent storage. When a pod consists of more than one container, the containers inside the pod can communicate with each other.
Deployments
A Kubernetes Deployment is an object that manages a set of pods to run a workload, such as defining the desired number of pods and how updates are applied. You can think of a Deployment as a wrapper around the pods.
Kubernetes Service Types
Kubernetes Services connect a set of pods to a single service endpoint and an IP address. Services provide routing between pods—for example, linking a front‑end application to the back‑end of an application. A Kubernetes Service is therefore a mechanism to expose an application both internally and externally. There are four service types in Kubernetes: ClusterIP, NodePort, LoadBalancer, and Ingress.
ClusterIP
ClusterIP is the default service type in Kubernetes. A ClusterIP provides an IP address that can be used only within the cluster.
NodePort
NodePort differs from ClusterIP in that it opens a port on every node in the cluster. A NodePort uses a port range between 30000 and 32767.
LoadBalancer
LoadBalancer is a Kubernetes service that, like a ClusterIP, allocates an IP address usable within the cluster. In addition, the LoadBalancer opens a port on each node (similar to a NodePort) but makes the service externally accessible and attempts to distribute incoming requests evenly across the nodes.
Ingress
Kubernetes Ingress is an API object that enables access to Kubernetes services from outside the cluster. An Ingress is a collection of routing rules that determine how users reach services inside a Kubernetes cluster.
Deploying Kubernetes¶
To depoy a kubernetes cluser choose Compute > kubernetes and select "Create Kubernetes Cluster".
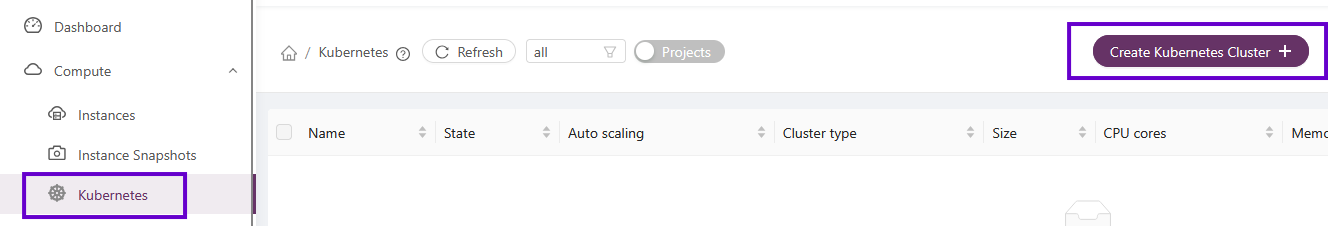
Fill in the fields as shown in the example below:
- Name: Choose a name for your Kubernetes cluster.
- Description: Provide a description (optional).
- Hypervisor: Required only when different types of hypervisors are available.
- Kubernetes version: Choose the version of Kubernetes to deploy.
- Compute Offering: Select the resource offering where the virtual machines will be deployed.
- Node root disk size: Specify the root disk size for each node.
- Network: Choose the network where Kubernetes will be launched.
- If the network field is empty, a new network will be created automatically. Make sure there are enough public IP addresses available.
- Cluster Size (Worker Nodes): Specify the number of worker nodes in the cluster (maximum of four).
- SSH keypair: If available, select your SSH key pair to use for logging in to the virtual machines.
When finished, you can begin deploying your Kubernetes cluster by clicking the OK button.
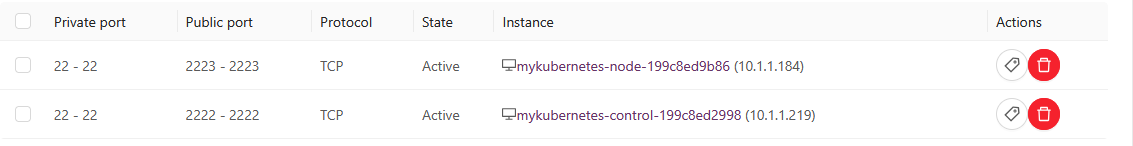
During deployment, the Kubernetes cluster automatically configures the required ports in the virtual firewall to enable access. See the following documentation for instructions on accessing the firewall ports and port-forwarding rules: setting up the firewall
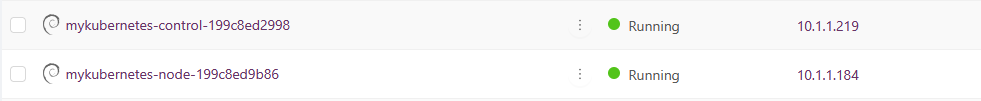
When deploying, you will see the instances required for Kubernetes appear under Compute > Instances.
Accessing Kubernetes¶
After the Kubernetes deployment, you can access your cluster using the CLI or the Kubernetes Dashboard UI.
Kubernetes Cluser config file¶
To access Kubernetes through the CLI, you need to download the Kubernetes cluster config file. To download the Kubernetes Cluster config file:
- In the left navigation menu select Compute > kubernetes.
- click on the cluster name.
- Click Access.
- Click the "Download Kubernetes cluster config" button and save the configuration file.

Using CLI¶
After saving the configuration file, you will need the kubectl command-line tool. The kubectl command-line tool uses kubeconfig files to find the information it needs to choose a cluster and communicate with the API server of a cluster.
You can download the kubectl tool for the cluster’s Kubernetes version from the Access tab as well.

After downloading the configuration file and the kubectl tool, you can access your Kubernetes cluster using the following command:
kubectl --kubeconfig /custom/path/kube.conf {COMMAND}
For Example:
List Pods
kubectl --kubeconfig /custom/path/kube.conf get pods --all-namespaces
List nodes
kubectl --kubeconfig /custom/path/kube.conf get nodes --all-namespaces
List services
kubectl --kubeconfig /custom/path/kube.conf get services --all-namespaces

Kubernets dashboard UI¶
To access the Kubernetes Dashboard, you need to run a local proxy. The local proxy secures access from outside the cluster. The kubectl proxy command creates a local server that forwards requests to the Kubernetes API server, enabling access to the Dashboard through a secure tunnel.
Before running the proxy, you must first download the Kubernetes cluster config file, as described in the documentation above.
Start the proxy with the following command: - kubectl --kubeconfig /custom/path/kube.conf proxy

You can now open the dashboard URL in the browser.
http://localhost:8001/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/

Token Creation for Dashboard¶
Linux/MacOS¶
Since Kubernetes v1.24.0, there is no auto-generation of secret-based service Account token due to security reason. You need to create a service Account and an optional long-lived Bearer Token for the service Account.
kubectl --kubeconfig /custom/path/kube.conf apply -f - <<EOF
apiVersion: v1
kind: ServiceAccount
metadata:
name: kubernetes-dashboard-admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin-user
namespace: kubernetes-dashboard
---
apiVersion: v1
kind: Secret
type: kubernetes.io/service-account-token
metadata:
name: kubernetes-dashboard-token
namespace: kubernetes-dashboard
annotations:
kubernetes.io/service-account.name: kubernetes-dashboard-admin-user
EOF
After running the above command, the token for dashboard login can be retrieved using the following command:
kubectl --kubeconfig /custom/path/kube.conf describe secret $(kubectl --kubeconfig /custom/path/kube.conf get secrets -n kubernetes-dashboard | grep kubernetes-dashboard-token | awk '{print $1}') -n kubernetes-dashboard

-
Windows¶
If you are using Windows, you need to paste the code below into a YAML file. This is because the here-doc syntax (<<EOF ... EOF), which works on Linux/macOS shells, does not work in Windows Command Prompt. In the example below, I created a file named dashboard-token.yaml.
apiVersion: v1
kind: ServiceAccount
metadata:
name: kubernetes-dashboard-admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin-user
namespace: kubernetes-dashboard
---
apiVersion: v1
kind: Secret
type: kubernetes.io/service-account-token
metadata:
name: kubernetes-dashboard-token
namespace: kubernetes-dashboard
annotations:
kubernetes.io/service-account.name: kubernetes-dashboard-admin-user
After adding the code to a YAML file, you can run the following command in a Command Prompt to generate the token:
kubectl --kubeconfig c:\custom\path\kube.conf apply -f C:\kubernetes\dashboard-token.yaml

You will need to use the following PowerShell command to retrieve the token:
$secretName = kubectl --kubeconfig C:\custom\path\kube.conf get secrets -n kubernetes-dashboard `
| Select-String "kubernetes-dashboard-token" `
| ForEach-Object { ($_ -split "\s+")[0] }
kubectl --kubeconfig C:\custom\path\kube.conf describe secret $secretName -n kubernetes-dashboard

After retrieving the Token you can paste this in the Kubernetes Dashboard and click the Sign in button.
